scale-tone
Introducing KeeShepherd.
Quick link to VsCode marketplace
I hate placing credentials (connection strings, access keys, secrets, passwords etc.) into config files (web.config, app.config, .env, local.settings.json etc.). Every time I do that I get nervous, because:
- I always forget where I left them. So they quickly get scattered across countless folders and devboxes, like lobsters crawling out of a trap. Difficult to rotate and difficult to cleanup.
- I always face the fear of accidentally exposing them during demo sessions. Unlike password fields in browsers, config files are just a text, and IDEs are not yet smart enough to automatically hide secrets in them.
- I’m always afraid of accidentally committing them to the repo.
.gitignorecertainly helps, but I still need to remember to configure it properly. - I always get bored when re-configuring them on a fresh new devbox (e.g. on GitHub Codespaces). And no, sharing config files with secrets via email is absolutely not an option.
Yes, it seems like we’re heading towards the bright passwordless future, but for us developers working with various cloud services and databases that future hasn’t arrived yet.
So as a temporary solution for the next decade or so I created KeeShepherd. This tool comes in form of a VsCode extension, and no, it is not a password manager. It does not store secret values, only cryptographically strong salted SHA-256 hashes of them, links to them (whether it is a link to an Azure Key Vault secret or to a secret accessible via Azure Resource Manager REST API, like Storage access keys), their lengths and positions in config files. Yet this information is enough for KeeShepherd to be able to:
-
automatically mask (hide) secret values once you open a config file:

-
(automatically) stash (aka replace with anchors like
@KeeShepherd(secret-name)) and unstash (aka do the opposite) them:
-
track their positions within a file, so that your config files remain absolutely editable;
-
show all your secrets in form of a list, thus giving your a central control point over them:

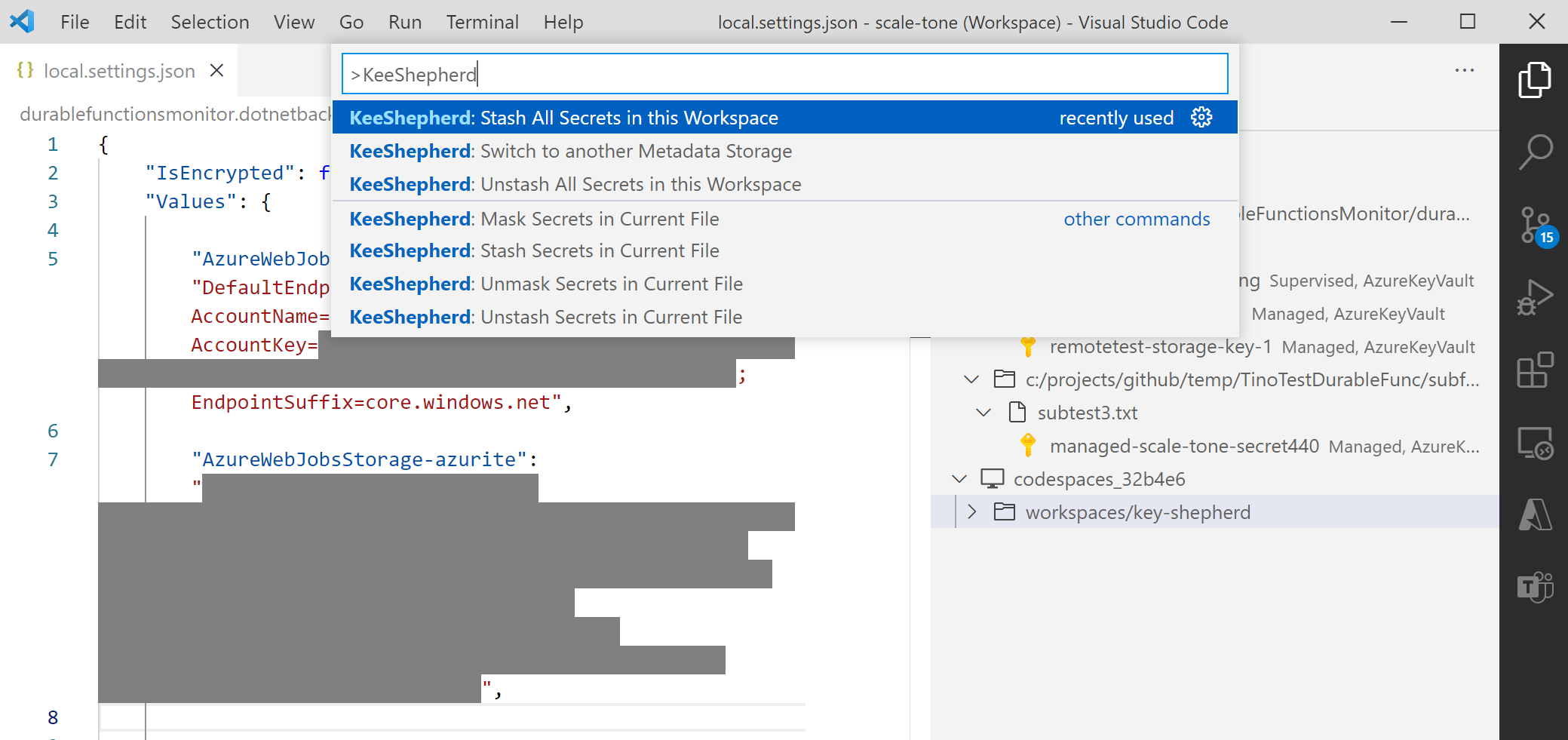
KeeShepherd is not yet able to detect your secrets automatically, so you’ll need to point it to them. That you do by:
-
Either inserting a secret at the current cursor position:

-
Or adding the selected secret value into KeeShepherd:

Insert operation by far supports Azure Key Vault, Azure Storage, Cosmos DB, Service Bus, Event Hubs, Event Grid, Azure Redis Cache, Application Insights and custom Resource Manager REST API URLs as secret sources, but more sources are on its way.
Add operation will suggest to also put the secret value into Azure Key Vault.
Two types of secrets are currently supported:
- Supervised. This is a lightweight form of it, just to remember where you left this secret value, let you navigate back to it at any moment and also automatically mask them when a config file is opened. Config files themselves are left unchanged.
- Managed aka stashable. Stashing does modifies your config files, since this is the whole point of it. Unstashing restores secret values by fetching them from wherever they’re actually stored, e.g. from Azure Key Vault.
It’s perfectly fine to mix both supervised and managed secrets in the same config file. A good strategy could be to mark real secrets (access keys, connection strings etc.) as managed (to keep them safe) and leave less important values like user names, application ids etc. as supervised (to make it easy to find them later).
Stashing/unstashing can be done either for a currently active file:

, for a folder:

or for the entire currently open workspace (including all subfolders):

KeeShepherd can also do automatic stashing/unstashing once you open/close a workspace. Default mode is to automatically stash and do not automatically unstash, but you can configure this via Settings:

Automatic stashing/unstashing seems to be the most secure form, it ensures that your secret values are only present in the config files while you’re actually working on the project (aka while a VsCode window is open). But this mechanism is, of course, not immune to VsCode accidental crashes, so better to explicitly check whether it all went as planned.
As I said before, KeeShepherd does not store your secret values. In its metadata store it only stores salted SHA-256 hashes of them and their “coordinates” aka file paths and last known positions. This metadata store can be in form of:
- Local JSON-files in VsCode’s global storage folder (
C:\Users\user-name\AppData\Roaming\Code\User\globalStorage\kee-shepherd.kee-shepherd-vscodeon Windows). - Shared Azure Table. This mode gives you a bird’s eye view of all your (and your teammate’s) secrets on all your devboxes, including GitHub Codespaces (yes, KeeShepherd extension works there as well).
KeeShepherd will ask you what metadata storage type you prefer at first run, but you can always change it later with Switch to Another Metadata Storage command:

All of this is only the beginning, of course. Many other new features are to be added in the next version(s), for example:
- More secret sources.
- Easily rotate (modify) secret values from ‘SECRETS’ view.
- More ways to visualize the list of secrets.
- … put your suggestions here …
Other incarnations of KeeShepherd, e.g. CLI version and/or plugins for other IDEs are also very much on the radar. But so far you’re very welcome to install it from VsCode marketplace and enjoy.